BLOGS

- Apr 28, 2023
- Qakbot Continues to Menace Corporate Environments
- Learn more about Qakbots and how they evade detection.

- Mar 30, 2023
- Protecting Against Malicious USB Devices
- Learn more about a drop attack and how to detect them.
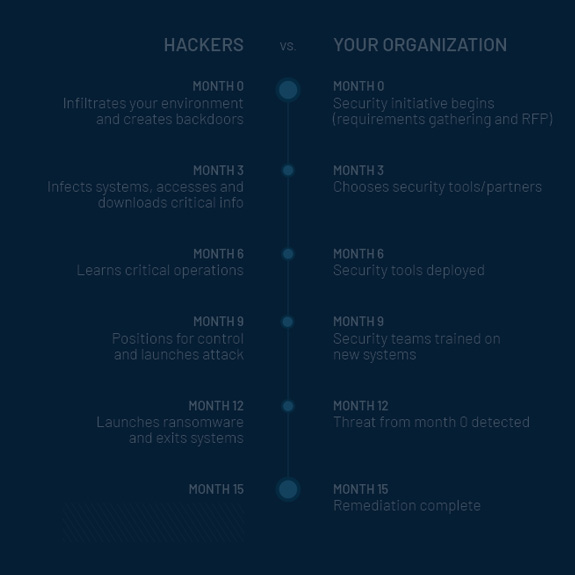
- Feb 9, 2023
- The Timeline of Security and The Secret to Why Cybersecurity Sometimes Fails
- Learn the role a timeline for security plays and how to avoid being easily hacked.

- Sep 30, 2022
- Bad Listening Harms Relationships and Cyber Programs
- Learn how Vigilant maintains secure networks & strong relationships with their secret weapon - listening.

- Jul 27, 2022
- Quick Security Wins for $0
- Learn how Vigilant has discovered simple and easy ways to combat ransomware attacks at no-cost.

- Apr 8, 2022
- Why US Based SOCs are Important to US Based Companies
- Learn why Vigilant is committed to having an all US-Based SOC and the importance of it.

- Feb 24, 2022
- FIRST TO DETECT BUT NEVER PUBLICIZE
- Learn how Vigilant discovered a Microsoft Exchange vulnerability before Microsoft with our Adaptive Intelligence Process.
- Jan 13, 2022
- GREAT SECURITY SOLVES UNEXPECTED PROBLEMS
- Learn how great security solves unexpected problems, shortens timeframes, and minimizes costs.
- Jan 11, 2022
- Recent Attacks Require An Updated Mindset
- Learn about the mindset that needs to developed in order to combat modern cyber attacks.

- Jan 3, 2022
- DIFFERENCE BETWEEN VULNERABILITY SCANNING AND PENETRATION TESTING
- Learn the differences between Vulnerability Scanning, Penetration Testing, and Red Teaming while learning which is best for your company.